How to Make Anything Signify Anything
William F. Friedman and birth of modern cryptanalysis
(accompanied by a poster insert)
William H. Sherman

For much of his long and largely secret career, Colonel William F. Friedman kept a very special photograph under the glass plate that covered his desk. As desks go, this one saw some impressive action. By the time he retired from the National Security Agency in 1955, Friedman had served for more than thirty years as his government’s chief cryptographer, and—as leader of the team that broke the Japanese PURPLE code in World War II, co-inventor of the US Army’s best cipher machine, author of the papers that gave the field its mathematical foundations, and coiner of the very term cryptanalysis—he had arguably become the most important code-breaker in modern history.[1]
At first glance, the photo looks like a standard-issue keepsake of the kind owned by anyone who has served in the military. Yet Friedman found it so significant that he had a second, larger copy framed for the wall of his study. When he looked at the oblong image, taken in Aurora, Illinois, on a winter’s day in 1918, what did Friedman see? He saw seventy-one officers, soon to be sent to the war in France, for whom he had designed a crash course on the theory and practice of cryptology. He saw his younger self at one end of the mysterious group of black-clad civilians seated in the center; and at the other end he saw the formidable figure of George Fabyan, the director of Riverbank Laboratories in nearby Geneva, where Friedman found not just his cryptographic calling but also his wife Elizebeth (flanked here by two other instructors from Riverbank’s Department of Ciphers). And he saw a coded message, hiding in plain sight. As a note on the back of the larger print explains, the image is a cryptogram in which people stand in for letters; and thanks to Friedman’s careful positioning, they spell out the words “KNOWLEDGE IS POWER.” (Or rather they almost do: for one thing, they were four people short of the number needed to complete the “R.”)
The photograph was an enduring reminder, then, of Friedman’s favorite axiom—and he was so fond of the phrase that some fifty years later he had it inscribed as the epitaph on his tomb in Arlington National Cemetery.[2] It captures a formative moment in a life spent looking for more than meets the eye, and it remained Friedman’s most cherished example of how, using the art and science of codes, it was possible to make anything signify anything. This idea will no doubt strike us as quintessentially modern, if not postmodern, but Friedman took it straight from the great Renaissance scholar-statesman Sir Francis Bacon (1561–1626), along with both the hidden motto in the image and the method used to convey it. In other words, the graduation photo from Friedman’s earliest course in military cryptanalysis is at once a tribute to Bacon’s philosophy and a master class in the use of his biliteral cipher.
Bacon devised this ingenious code in the late 1570s (when he spent three years in the entourage of the English ambassador in France), but he did not describe its workings until 1623.[3] The cipher was based, as the name “biliteral” suggests, on a system using only two letters—or, more precisely, one where each letter in the alphabet is represented by some combination of a’s and b’s. When Bacon realized that it was possible to represent all twenty-six letters in permutations of only two by using groups of five, he generated the following key:[4]
A = aaaaa
B = aaaab
C = aaaba
D = aaabb
E = aabaa
F = aabab
G = aabba
H = aabbb
I/J = abaaa
K = abaab
L = ababa
M = ababb
N = abbaa
O = abbab
P = abbba
Q = abbbb
R = baaaa
S = baaab
T = baaba
U/V = baabb
W = babaa
X = babab
Y = babba
Z = babbb
The crucial point in Bacon’s system is that the a’s and b’s in the ciphered text are not represented by those actual letters. If they were (using what is known as a straightforward substitution cipher[5]), a message reading “Hi” would simply appear as “aabbb abaaa”: anyone intercepting the text would quickly see that it was in code, and—given enough text and time—would easily discover the key. His way around this problem was as powerful as it was simple: he allowed the a’s and b’s in his system to designate the different forms of anything that can be divided into two classes, sorts, or types (which Bacon referred to as the a-form and the b-form).

If our “infolded” writing (or plain-text) is “Hi,” we simply need to create an “infolding” text (or cover-text) that says anything we want it to but is ten letters long, with the third, fourth, fifth, and seventh letters represented by b-types and the rest by a-types. These types might, indeed, be typographical, distinguished, say, by bold-face versus regular:
brooklyn ny
↓
aabbb abaaa
↓
h i
Or we might toggle between two different fonts (which Bacon called a “bi-formed alphabet”). In the example supplied by Bacon himself, a secret agent is warned to flee through a deceptive cover-text:
Do not go til I come
↓
aabab ababa babba
↓
f l y
The hidden message here is doubly secure because our cover-text can say the opposite of what we mean while looking like plain (if poorly printed) text.[6]
But Bacon added a further twist to the ancient art of steganography, the general name for the practice of concealing messages through the use of disguise and deception.[7] In the biliteral cipher, the cover-text need not, in fact, be “text” at all: the a’s and b’s can be represented by two types of anything—pluses and minuses, flowers of different kinds or colors, even (literally) apples and oranges—and this, for Bacon, is what gives his biliteral system the greatest power of all,
which is to signifie omnia per omnia [anything by means of anything]. … And by this Art a way is opened, whereby a man may expresse and signifie the intentions of his mind, at any distance of place, by objects which may be presented to the eye, and accommodated to the eare … as by Bells [and] Trumpets, by Lights and Torches … and any instruments of like nature.[8]
When Friedman assembled his students and colleagues in front of the Aurora Hotel to give them a living illustration of Bacon’s art, he used the most natural instrument of all, their bodies, simply asking the a’s to face the camera and the b’s to look away. So the seated group of which he was a part would form the sequence “abaab”—which would be a k (but not, as it happens, the initial “K” in Bacon’s axiom).
It is unlikely that Bacon’s cipher system was ever used for the transmission of military secrets, in the seventeenth century or in the twentieth. But for roughly a century from 1850, it set the world of literature on fire. A passion for puzzles, codes, and conspiracies fueled a widespread suspicion that Shakespeare was not the author of his plays, and professional and amateur scholars of all sorts spent extraordinary amounts of time, energy, and money combing Renaissance texts in search of signatures and other messages that would reveal the true identity of their author. Even after the recent publication of James Shapiro’s comprehensive history of the authorship controversy, Contested Will, it is difficult for us to appreciate the depth of conviction—among writers as diverse and as distinguished as Mark Twain, Walt Whitman, Sigmund Freud, Henry James, Henry Miller, and even Helen Keller—that Shakespeare’s texts contained the secret solution to what was widely considered to be “the Greatest of Literary Problems.”[9] Bacon became (for a while) the leading candidate, and his biliteral cipher—Renaissance England’s first and clearest statement about how to hide texts within texts—seemed to offer the “Baconians” (as his champions were known) the key that everyone was looking for.
As late as 1946, the long-running radio program The New Adventures of Sherlock Holmes could air an episode called “The Singular Affair of the Baconian Cipher,” in which Holmes and Watson set off for Penge in search of “a paralyzed Baconian scholar” who has summoned them with a peculiar piece of printing in their morning newspaper.[10] Friedman’s own introduction to the wonderful world of codes had come through Edgar Allan Poe’s story “The Gold Bug,” which he read as a child, and he later suggested that most people came to cryptography through the genre of detective fiction.[11] But in the early years of the twentieth century, the Baconians thought they had found a truth that was stranger than fiction, and a schoolteacher from Michigan named Elizabeth Wells Gallup inspired a generation of readers to plunge into the plays of Shakespeare with Bacon’s biliteral cipher in hand.
Nobody was more excited by Gallup’s alleged discoveries than George Fabyan, the eccentric heir to the country’s largest cotton-goods firm. Fabyan brought Gallup to his private estate at Riverbank, on the Fox River just west of Chicago. He had the main building redesigned by Frank Lloyd Wright and gradually added a Japanese garden, a Roman-style swimming pool, a working lighthouse, an open-air zoo (with a gorilla named Hamlet), and a Dutch windmill moved brick-by-brick at outrageous expense. Gallup joined an avant-garde faculty of scientists dedicated, as Fabyan put it, to “wresting from Nature, her secrets.” Mr. B. E. Eisenour served as dean and director of research in physics, bringing Professor Wallace Sabine from Harvard to continue his pioneering work on architectural acoustics; a Dr. Scott carried out experiments in the medicinal uses of radioactive elements, and a Dr. Henderson worked on hoof-and-mouth disease; and J. A. Powell, former editor of the University of Chicago Press, took up a chair in typography. Gallup was equipped with a team of assistants (including Elizebeth Smith, a young Shakespearean plucked from the stacks of the Newberry Library) and a photographic workroom, where she presided over an “American Academy of Baconian Literature,” publishing new work on the biliteral cipher and developing a correspondence course on literary cryptology.
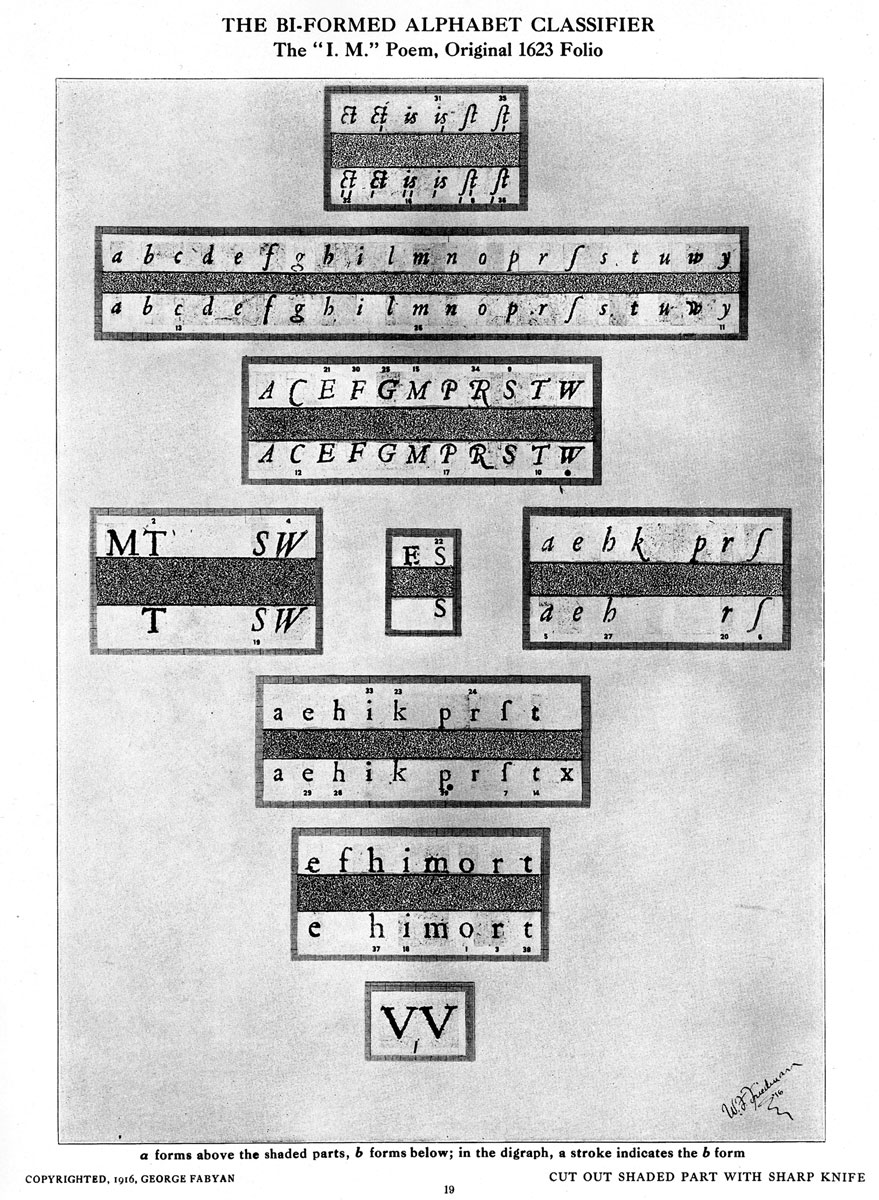
In September 1915, Fabyan lured Friedman away from a PhD in plant biology at Cornell, setting him up as director of the Department of Genetics and putting him to work on the propagation of wheat. But Friedman’s interest in photography and bibliography (not to mention Elizebeth Smith) soon brought him into Gallup’s Department of Ciphers, where he created many of the images used in Riverbank’s Baconian publications. His signature is found in the lower right corner of many of the team’s studies of Elizabethan letterforms, and he seems to have had a hand in most of their “alphabet classifiers,” standardized templates designed to be placed over Shakespeare’s plays and poems with visual aids to help readers sort the haphazard printing into a-types and b-types, allowing them to see the messages that Bacon had hidden behind the most famous of all texts. While he would soon lose faith in the methods and the purpose of Gallup’s project, Friedman’s Baconian initiation was of the utmost importance, both for his personal career and for the development of cryptography as a field.

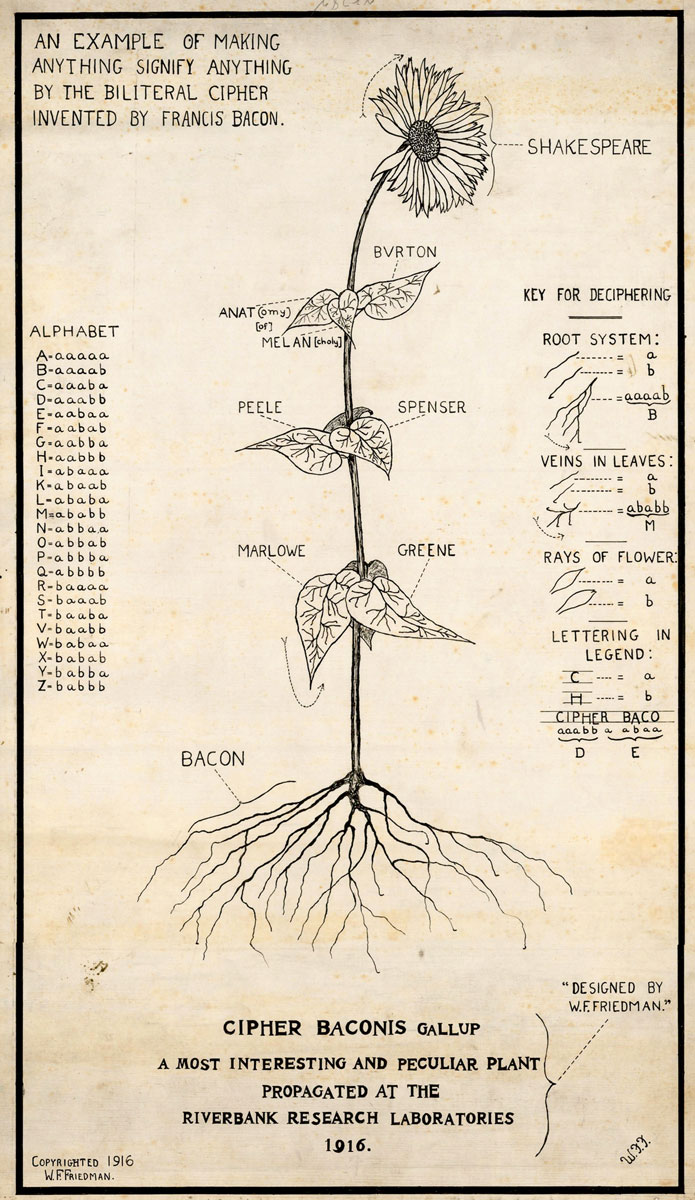
I have recently stumbled across the archive of Friedman’s years at Riverbank (with working notes and manuscript drafts that Friedman himself sought in vain to recover), and it documents his transition from genetics to cryptology and from literary to military codes. It reveals an intuitive grasp of cipher systems that must have been breathtaking: Friedman’s instant ability to work—and play—with the biliteral cipher makes his early encounter with Bacon look like Alice’s encounter with the looking glass. Sometime in 1916 he designed a card that Gallup and her team used for internal notes and letters to the world beyond Riverbank. It is a botanical drawing of a flower with the witty caption, “CIPHER BACONIS GALLUP / A MOST INTERESTING AND PECULIAR PLANT PROPAGATED AT THE RIVERBANK RESEARCH LABORATORIES / 1916.” But Friedman left behind a second version of the image used in teaching, where he reveals that everything on it—including the flower—says something else, using Bacon’s now familiar method. He added a new caption at the top, describing it as “An example of making anything signify anything by the biliteral cipher invented by Francis Bacon.” The roots of the flower take two forms, bearing the name “Bacon”; the leaves have lines of two types, which yield the names of various Elizabethan authors and books; and the petals can be split into notched and unnotched forms, spelling out “Shakespeare.” Even the printed caption at the bottom turns out to be a biliteral cipher, confirming Friedman’s authorship of the design (as if there could be any doubt).
Another design from the same year used a more innocent cover-text, the sheet music for Stephen Foster’s extremely popular nineteenth-century song, “My Old Kentucky Home, Good Night.”[12]Only the tell-tale caption at the bottom, “An example of making anything signify anything,” tips us off to the Baconian cipher it contains. This time Friedman left no key, but once we notice that some of the notes have small gaps in them (b-types), and some are whole (a-types), it does not take long to extract the secret message: “ENEMY ADVANCING RIGHT / WE MARCH AT DAYBREAK.”
By the middle of 1917, the enemy was indeed advancing, and it was clear that the US military needed cryptographic expertise of a kind and on a scale that it did not yet have. As the government prepared to enter World War I, it turned to the cryptographic think-tank created by Fabyan and sent a stream of coded correspondence to be broken along with a series of units to be trained. Friedman himself would soon be commissioned and sent off to France, and while he worked for a few more years at Riverbank after he returned, by the early 1920s he and his wife had moved to Washington for good, where they pursued their long careers with the cryptographic agencies they helped to create. But they kept in close contact with the network of Baconians and in 1954 finished a remarkable study of Gallup and others: it was published in 1957 as The Shakespearean Ciphers Examined, and it almost single-handedly put an end to the craze for amateur cryptography in the service of anti-Shakespearean arguments.
But even in that skeptical (and often scathing) book, the Friedmans express their admiration for Bacon’s contribution to the field they made their own. Indeed, they remind us of how much the modern world owes to him. Many of the twentieth century’s major developments in artistic practice and scientific method derive either from the ability to make anything signify anything or from the problems of mind and meaning this posed. Friedman’s early applications of probability to cryptography (like new approaches to psychoanalysis, structural linguistics, literary criticism, and so on) were designed in part to answer the question, “If anything can signify anything, then how do we know what anything means?” And in an introductory lecture written in the late 1950s, Friedman finally spelled out the connection between the a’s and b’s of Bacon’s biliteral cipher and the zeros and ones that were creating a new digital age: “Bacon was, in fact, the inventor of the binary code that forms the basis of modern ... computers.”[13]
Computers have increased our ability to make anything signify anything in ways that Friedman could not have predicted. A Google search for steganography reveals a whole world of digital tools and communities that combine traditional cryptography with cutting-edge computation—and its applications are both more innocent and more sinister than anything produced by the Baconians. Unused bytes and pixels in files can contain huge amounts of invisible information, and by using basic programs and simply changing the settings in a display, a tree can become a cat, a cat can tell us to blow up a bridge, and an oil painting of a whaling expedition can carry the entire text of Moby Dick.[14] The codes of the computer age contain more a’s and b’s than were dreamt of in Bacon’s philosophy.
- David Kahn concludes the best account of Friedman’s contributions to the field by granting him “the mantle of the greatest cryptologist” of all time; see The Codebreakers: The Story of Secret Writing (New York: Macmillan, 1967), p. 393. Ronald Clark’s popular biography, The Man Who Broke PURPLE (Boston: Little Brown & Co., 1977), offers a useful introduction to Friedman’s papers at the George C. Marshall Foundation, on the campus of the Virginia Military Institute in Lexington, Virginia. The library’s website marshallfoundation.org/library/collection.html (accessed 30 July 2012) now features a comprehensive guide to the Friedman Collection produced by VMI historian Rose Mary Sheldon, and I am grateful both to Dr. Sheldon and to the staff at the Marshall Foundation—especially Paul Barron and Jeffrey Kozak—for their help and hospitality.
- See arlingtoncemetery.net/wfried.htm. Accessed 26 November 2010.
- Francis Bacon, De Dignitate & Augmentis Scientiarum, in Opera Francisci Baronis de Verulamio (London: John Haviland, 1623); first translated into English by Gilbert Wats as Of the Advancement and Proficiencie of Learning (Oxford: Leonard Lichfield, 1640). The discussion of ciphers is found in book 6, chapter 1. On Bacon’s years in France, and his close contact there with “the grand master of intelligence ciphers, Thomas Phelippes,” see Lisa Jardine and Alan Stewart, Hostage to Fortune: The Troubled Life of Francis Bacon 1561–1626 (London: Victor Gollancz, 1998), chapter 2.
- Note that the doubling up of I/J and U/V is not a shortcut: in Bacon’s day, they were effectively the same letter, meaning that the English alphabet had only twenty-four letters. Using groups of five yielded thirty-two permutations of a’s and b’s, more than enough for even the full modern alphabet.
- In his Six Lectures on Cryptology, produced for the National Security Agency in the late 1950s and recently reissued by the NSA’s Center for Cryptologic History, Friedman offered the following distinction: “Technically, there are only two distinctly different types of treatment that may be applied to written plain text to convert it into a cipher, yielding two different classes of ciphers. In the first, called transposition, the letters of the plain text retain their original identities and merely undergo some change in the relative positions, with the result that the original text becomes unintelligible. … In the second, called substitution, the letters of the plain text retain their original relative positions but are replaced by other letters with different sound values, or by symbols of some sort, so that the original text becomes unintelligible.” See the Center for Cryptologic History, The Friedman Legacy (Fort Meade, MD: National Security Agency, 1992), pp. 11–13.
- I have adapted this example from Bacon’s Of the Advancement and Proficiencie of Learning, pp. 266–268. Here, we have used Palatino for a’s and Univers for b’s, but Bacon’s original fonts are far closer in style—making the coded text less likely to raise suspicion but also harder to decipher.
- The practice went back to ancient Greece, but the term was first used in the 1490s by Johannes Trithemius—author of the first printed book on cryptography.
- Bacon, Of the Advancement and Proficiencie of Learning, pp. 265–266. In an earlier discussion of ciphers (from the 1605 first edition of the book), Bacon described “the highest Degree” of ciphering as the ability “to write OMNIA PER OMNIA; which is undoubtedly possible, with a proportion Quintuple at most, of the writing infoulding, to the writing infoulded, and no other restrainte whatsoeuer” (Book 2, fol.61r), but he did not describe his own invention for doing so.
- James Phinney Baxter, The Greatest of Literary Problems (Boston: Houghton Mifflin Co., 1915); James Shapiro, Contested Will: Who Wrote Shakespeare? (New York: Simon & Schuster, 2010).
- This episode was broadcast on 27 May 1946, and it marked Basil Rathbone’s final appearance as Sherlock Holmes. The script betrayed more than a passing familiarity with Baconian scholarship: Holmes takes Ignatius Donnelly’s Great Cryptogram (1888) as common knowledge and offers a casual endorsement of the anti-Stratfordian position.
- William F. Friedman, “Edgar Allan Poe, Cryptographer,” American Literature, vol. 8, no. 3 (1936), pp. 266–280. See also Shawn James Rosenheim, The Cryptographic Imagination: Secret Writing from Edgar Poe to the Internet (Baltimore: The Johns Hopkins University Press, 1997), chapter 6.
- The song was first published in 1853 and became the state song of Kentucky in 1928. The version used by Friedman was published in 1903 as part of The Century Collection of Popular Selections for Mandolin and Guitar.
- The Center for Cryptologic History, The Friedman Legacy, p. 46.
- See en.wikipedia.org/wiki/Steganography and flickr.com/photos/krazydad/257804202. Both accessed 26 November 2010.
William H. Sherman is director of the Centre for Renaissance & Early Modern Studies at the University of York, the author of John Dee (University of Massachusetts Press, 1995) and Used Books (University of Pennsylvania Press, 2007), and the editor of plays by Shakespeare, Jonson, and Marlowe. He is currently writing a book that he is trying not to call The Bacon Code.